🇨🇦
- 1 Post
- 22 Comments

 1·12 hours ago
1·12 hours agoIt was all positive until the guy below me came in throwing insults. Then people started piling downvotes on both…

 24·15 hours ago
24·15 hours agoYou’re not required to run your own instance on your own hardware; you’ve just got to find an existing instance with an admin team you’re comfortable with, create your community there and recruit moderators just like you would on Reddit.

 1622·19 hours ago
1622·19 hours agoPotato, potato…
Whether we call them ‘undocumented commands’ or a ‘backdoor’, the affect is more or less the same; a series of high-level commands not listed within the specs, preventing systems engineers/designers from planning around vulnerabilities and their potential for malicious use.

 24·2 days ago
24·2 days agoJust knowing who those two people are requires education and we can’t have that.
Plus the sexual references? Double whammy; Ban approved.

 3813·6 days ago
3813·6 days agoHonestly; I’m impressed they both messaged you and gave you options.
Usually you wouldn’t find out until the mailman is demanding payment for the package he’s holding hostage in front of you.
deleted by creator

 4·6 days ago
4·6 days agoDon’t forget French Toast


 3·6 days ago
3·6 days agoI definitely recommend it, particularly using docker compose. It’s made it incredibly easy to add, remove, and modify software installs; keeping everything independent and isolated from each other.
This also makes backups and rolling back updates to individual projects much easier when you do run into problems.

 1·6 days ago
1·6 days agoHmm, I wonder if the failed updates are only direct installs vs docker.
I run two piholes, a primary on a rpi 3b running pios, and a secondary on my main server. Both are installed via docker and both updated without issue (besides the password thing).
I like having the primary DNS on a separate machine; it’s kind of important and I like to mess with the main server a lot…

 3·7 days ago
3·7 days agoInteresting; I’ll definitely have to keep that in mind. Much cheaper than getting basically a whole new set of hdds at almost $30/tb (new nas-grade drives, not referbs).
Thanks!

 3·7 days ago
3·7 days agoWhat hardware are you using to read/write tape, and what does that cost you?
I’ve got around 30tb that I need to shift off of a Drobo at some point so I can repurpose the drives into a proper RAID setup that isn’t a closed source black-box from a dead company (that was a poor choice, 6 years ago 🙁). Keeping an eye out for solutions for when I get around to fixing that mess.

 2·7 days ago
2·7 days agoI wonder why so many people had issues with the v6 pihole update.
I pulled the new docker container and it ran overtop the previous version just fine. The only issue I had was I had the admin password set to empty via an env variable and that variable name changed. Took like 10 min to find and fix. The rest migrated perfectly.
Now I’m just waiting on orbital-sync to add v6 support, but that’s just around the corner and not that critical.

 11·7 days ago
11·7 days ago95% of things I just don’t expose to the net; so I don’t worry about them.
Most of what I do expose doesn’t really have access to any sensitive info; at most an attacker could delete some replaceable media. Big whoop.
The only thing I expose that has the potential for massive damage is OpenVPN, and there’s enough of a community and money invested in that protocol/project that I trust issues will be found and fixed promptly.
Overall I have very little available to attack, and a pretty low public presence. I don’t really host any services for public use, so there’s very little reason to even find my domain/ip, let alone attack it.

 30·7 days ago
30·7 days agoLooking at openspeedtests github page, this immediately sticks out to me:
Warning! If you run it behind a Reverse Proxy, you should increase the post-body content length to 35 megabytes.
/edit;
Decided to spin up this container and play with it a bit myself.
I just used my standard nginx proxy config which enables websockets and https, but I didn’t explicitly set the max_body_size like their example does. I don’t really notice a difference in speed, switching between the proxy and a direct connection.
So, That may be a bit of a red herring.

 1·13 days ago
1·13 days agoPublic IPV4 here. It’s not static, but very rarely rotates. DDNS ftw.
Telus Residential in Canada.

 0·13 days ago
0·13 days agoThis part always confuses me, so I won’t be able to give specifics; just a general direction. Most guides explain how to route traffic from a vpn client to the lan of the vpn host. You need to route traffic from the vpn host/lan to a client of the vpn.
You need to change the routing table on the VPS, adding a static route to route traffic heading for your VPNs subnet to the VPN host instead of out the default gateway.
How exactly to do that I’ll have to leave to someone else unfortunately. Network config confuses the hell out of me.

They don’t let you specify in the ‘edit suggestion’ what it should be; but they let you add images.

/edit submitted one for every park in BC.

I’m not seeing this at all.
Provincial Parks in BC are all still called ‘xyz provincial park’.
If you explicitly search for ‘state park’ all the provincial ones come up, but there’s nothing in any of their details mentioning ‘state’ in anyway.
/edit: found it.
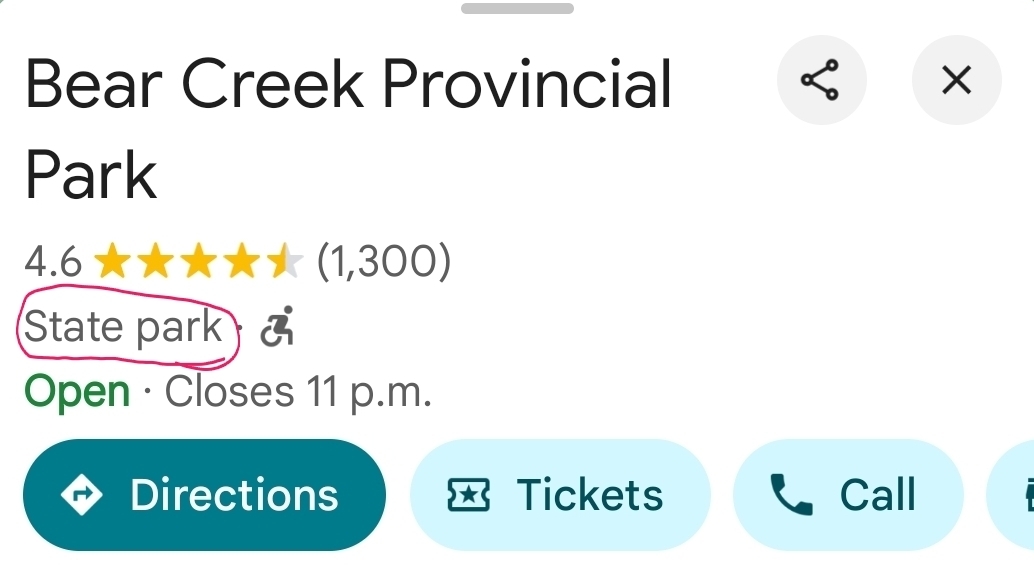
It’s subtle, but it’s there.


? That’s a bizarre response.
No one here is trying to fleece you. People are suggesting ways to run your own instance as that’s the major difference between Reddit and Lemmy; you’re not obligated to use someone else’s hardware or be subject to their rules, you can setup your own systems and have a bit more freedom. Reddit doesn’t give you that option.
Your account is subject to the rules of the instance it was created on, as well as the rules of each community you’re interacting with. If you run afoul of the admins for your instance, you can be banned, losing access to that account completely.
If you were to run your own instance; no single admin could ban your entire account if you pissed them off. You can still be blocked from communities or entire instances if you don’t play nicely with others, but you won’t lose the account so you can still use it in other instances/communities.
For most people this isn’t really necessary; but lemmy also has a pretty large number of tech nerds that like to self-host our own services, so you’ll get quite a bit of ‘heres how you can do it yourself’ type responses.
Unlike reddit, you can just setup your own space on your own hardware completely under your own control, if you don’t like what’s available.